Projects/Lidl Balkonkraftwerk Hacking: verschil tussen versies
kGeen bewerkingssamenvatting |
kGeen bewerkingssamenvatting |
||
| Regel 91: | Regel 91: | ||
== Esphome == | == Esphome == | ||
[[File:Lidl-Balkonkraftwerk-HASS-Sensors.png|200px|thumb|Stats shown in Home Assistant]] | |||
I have started building out an [https://git.polyfloyd.net/polyfloyd/esphome-config/src/branch/main/lidl-balkonkraftwerk.yaml Esphome configuration]. | I have started building out an [https://git.polyfloyd.net/polyfloyd/esphome-config/src/branch/main/lidl-balkonkraftwerk.yaml Esphome configuration]. | ||
Versie van 7 nov 2025 10:12
| Project Lidl Balkonkraftwerk Hacking | |
|---|---|
| Naam | Lidl Balkonkraftwerk Hacking |
| Beschrijving | ESP32 hacking |
| Website | https://www.lidl.nl/p/tronic-balkon-zonnepanelen-starterset-400-w/p100387536 |
| Start | 2025-10-25 |
| Contact | Polyfloyd |
| Status | Production |
I bought a solar power set from the Lidl in Germany for just 200 euros. A decent deal for 370 Wp panels, a microinverter and some mounting brackets.
On problem: the microinverter runs Tuya, which is notoriously connected to Chinese clouds. The inverter can be used without setting up network connectivity and the Tuya app, but I would like to have stats from this device in Home Assistant.
So let's hack it!
Teardown
The OEM manufacturer and model is EWAY-VNV6204. Eway makes more power electronics such as car chargers. There are a couple more models in this series such as the EWAY-VNV6208 where the last number corresponds to the wattage.
What is really neat is that the MCU responsible for network connectivity is an ESP32-C3 which I am familiar with. Moreover, it has a 4-pin header right next to it which is most likely UART and a physical push button labeled "BURN" which may very well be a button to put the ESP in flashing mode.
Getting In

The pad on the UART header farthest from the ESP is connected to a large copper plane. With a continuity test from a multimeter I was able to conclude that this is a ground plane. The two middle pins have thin traces leading to the ESP which means that these are the RX/TX lines. The last pad is probably VCC, I did not measure it.
The board is powered from the DC/solar side. The Lidl Tuya app reports the DC voltage when the sun is hitting the panels, which usually is around 26 volts in slightly overcast weather conditions. The EWAY specs state that the maximum input voltage for this device is 60 volts. Hooking up some probes to the neatly exposed cable connections to a lab power supply with 20V made the board power up.

Connecting the UART to a USB-dongle gave ASCII output! Hurray! The baudrate is 115200, which is the default for ESP devices.
Holding the BURN button while power cycling triggers the ESP to enter its ROM flashing mode, with which I was able to make a dump of the whole 4M firmware.
Reverse Engineering the ROM
Shoutout to Shiz from Revspace for helping me to get started with Ghidra! o7
I then plowed through the ROM for a few days. I had never done reverse engineering for binaries, so this was a first fun project to discover that. It's quite fun to do. Every function and variable that I identify gives a little dopamine hit. It's a flow-state zen which is similar to programming. I hit a few dead ends in the firmware until I figured out the best way to approach this:
- Find the ESP-IDF functions by searching for their log strings and printfs.
- Find out which of those IDF functions are doing some kind of IO
- Find out what kind of routines are making those function calls
It turned out that really the only kind of IO this device ever does is communicating over its UART1 peripheral (this is distinct from its debugging interface which is UART0).
The peripheral connected to UART1 is wired as GPIO6=TX, GPIO7=RX.
There is something connected to GPIO4 which according to the firmware dump seems to be a LED. However, there is no LED visible on the top side of the PCB. The only LED at all on this device is a status LED controlled by the MPTT which is multi-color.
Protocol
A basic communication frame consists of a 1 byte header that is 0xFA, followed by the contents and is terminated by a 1 byte inverted XOR-sum checksum and 0xFB.
The communication is rather unreliable, validating the checksum is a must.
Retrieving hardware/software info
>>> FA:01:06:00:F8:FB
^^ checksum
^^ ^^ cmd
<<< FA:01:06:0B:04:00:20:1E:17:DE:FB
^^ checksum
^^ software version
^^ hardware version
^^ rated power
Reading sensor values
>>> FA:10:01:00:EE:FB
^^ checksum
^^ ^^ command
<<< FA:10:14:12:09:F4:01:01:0B:52:04:29:01:84:01:D7:00:C2:00:00:00:00:00:F1:FB
^^ checksum
^^ ^^ ^^ ^^ integral of power-something
^^ ^^ temperature * 10
^^ ^^ dc current * 100
^^ ^^ dc voltage * 10
^^ ^^ dc power * 10
^^ operational status (0 = off, 8 = starting, 11 = active)
^^ ^^ ac frequency * 10
^^ ^^ ac voltage * 10
Esphome
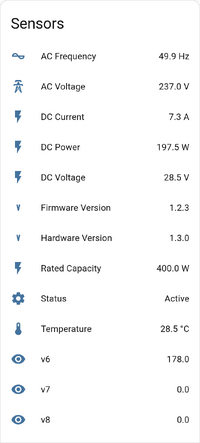
I have started building out an Esphome configuration.





